Foundations of Threshold Cryptography and MPC
This first module introduces the essential foundations of threshold cryptography and Multi-Party Computation (MPC). It explains how these approaches reshape key management in digital systems, especially in the context of cryptocurrency wallets. The discussion covers the theoretical background of threshold schemes, the operational principles of MPC, and why these concepts matter in securing private keys. By the end of this module, learners will understand the core mechanics that enable threshold-based wallets and how they differ from traditional approaches to cryptographic key storage.
What Is Threshold Cryptography?
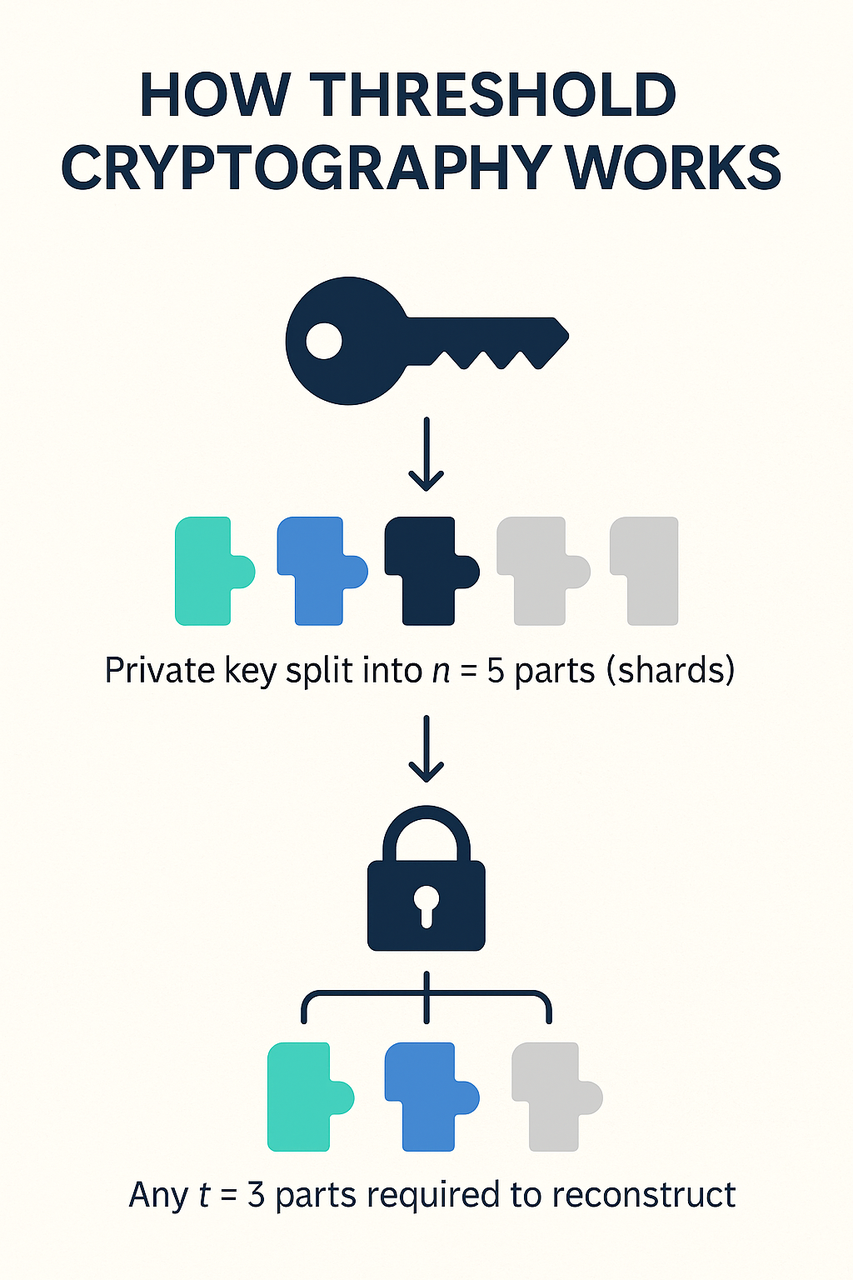
Threshold cryptography is a branch of cryptographic science that distributes a secret, usually a private key, into multiple parts or shares. The secret can only be reconstructed or used if a predefined number of shares, known as the threshold, are combined. This is often described in terms of a (t,n)(t, n)(t,n) scheme, where a secret is divided into nnn shares, and any ttt of them are sufficient to perform a cryptographic operation, such as signing a transaction. The design ensures that no single participant holds the full secret, reducing the risk of compromise from theft, hardware failure, or malicious intent.
The origin of threshold cryptography is closely tied to secret-sharing systems, particularly Shamir’s Secret Sharing (SSS), introduced in 1979. Shamir’s method allowed a secret to be mathematically split into several parts, ensuring that only the threshold number of shares could reveal the secret. However, modern threshold cryptography extends beyond static reconstruction. Rather than reassembling the private key in one place, threshold schemes allow cryptographic operations—such as digital signatures or decryption—to be performed collaboratively by multiple parties without ever recombining the full secret. This enhancement makes threshold systems far more secure for digital asset custody, where even brief exposure of a full private key could lead to catastrophic loss.
Multi-Party Computation (MPC)
Multi-Party Computation, or MPC, is a broader cryptographic framework that enables multiple parties to jointly compute a function over their private inputs without revealing those inputs to one another. In the context of digital wallets, MPC ensures that private key material is never reconstructed in full but instead remains distributed across several participants. Each participant performs partial computations on their share, and the results are combined to yield a valid cryptographic output, such as a signature, without any party ever accessing the complete private key.
The critical strength of MPC lies in its ability to remove the concept of a single point of failure. In traditional systems, whoever controls the private key controls the funds. If the key is lost, stolen, or corrupted, the consequences are irreversible. MPC eliminates this fragility by ensuring that no single device, server, or person has enough data to compromise the wallet. Even if one share is compromised, the threshold cannot be reached without cooperation from the required number of other participants. This property makes MPC highly resilient against both external cyberattacks and internal risks such as insider fraud.
Threshold Signatures
One of the most important applications of threshold cryptography and MPC in wallets is threshold signatures. In a threshold signature scheme, multiple parties collaboratively generate a valid digital signature without ever revealing their secret shares. Each party uses its share to compute a partial signature, and these partial outputs are combined into one final signature that is indistinguishable from a standard digital signature. This design allows blockchains and decentralized applications to accept threshold signatures without needing to modify their protocols.
The indistinguishability of threshold signatures from conventional signatures is critical. It means that wallets using MPC and threshold schemes remain compatible with existing blockchain networks, which expect specific signature formats such as ECDSA or EdDSA. As a result, threshold cryptography can be adopted without requiring protocol-level changes, making it practical for immediate deployment across a wide variety of digital assets.
Why Threshold Cryptography Matters for Wallets
Threshold cryptography and MPC address the most significant vulnerabilities of traditional crypto wallets. Conventional wallets rely on a single private key or, at best, a seed phrase that can regenerate the key. These systems create a fragile dependency: the compromise of one element is enough to endanger the entire wallet. For institutional custodians, exchanges, or even individuals managing substantial holdings, this model poses unacceptable risks.
Threshold-based wallets remove the single point of failure by distributing key material across different parties or devices. This may involve multiple servers in different geographic locations, a combination of user devices and institutional co-signers, or hybrid setups that include secure hardware modules. The user still experiences the wallet as a single interface, but behind the scenes, the signing process requires cooperation among several entities. This creates a more robust security environment that is resilient against hacking, insider threats, and physical device loss.
Moreover, threshold cryptography introduces flexibility in governance. Institutions can design signing policies that require specific subsets of participants to authorize transactions. For example, a treasury department might require that three out of five executives sign off on large transfers, while routine transactions could be approved with fewer shares. These governance mechanisms are embedded directly into the cryptographic layer, making them more secure and less prone to circumvention than traditional policy enforcement.
Threshold Cryptography Versus Legacy Models
The value of threshold cryptography becomes clearer when compared with older models of wallet security. Seed phrase backups, still widely used, place the entire recovery mechanism in a single string of words. Anyone who accesses the phrase gains full control of the wallet. Hardware wallets improve security by isolating private keys from general-purpose devices, but they still revolve around a single key that must be backed up somewhere. Multisignature wallets distribute control across multiple keys, but they do so on-chain, which increases transaction costs and reduces privacy because the signing structure is visible to anyone examining the blockchain.
Threshold cryptography, in contrast, combines the advantages of distribution with privacy and cost efficiency. By producing a single standard signature from a collaborative process, it preserves user privacy and avoids the higher transaction fees associated with multisignature operations. The distribution of key shares offers security superior to both seed phrases and single-device hardware solutions. This unique balance of security, privacy, and usability explains why threshold cryptography and MPC are gaining rapid adoption across both institutional and retail wallet providers.





